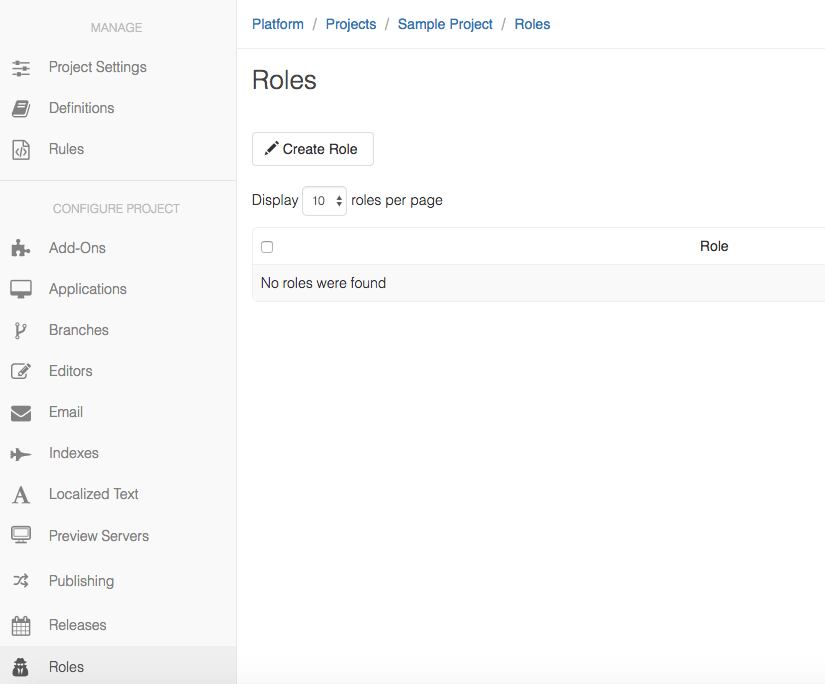
Create a new Role
The Roles for a Project can be managed on the Roles page. For reference, here are the default Roles available:
Let's take a look at the list of the default roles:
| Roles | Description |
|---|---|
| Collaborator | “CONNECT”, “READ”, “CREATE_SUBOBJECTS”, “UPDATE”, “DELETE” |
| Connector | “CONNECT” |
| Consumer | "CONNECT”, “READ” |
| Contributor | “CONNECT”, “READ”, “CREATE_SUBOBJECTS” |
| Editor | “CONNECT”, “READ”, “UPDATE”, “DELETE” |
| Impersonator | “IMPERSONATE” |
| Manager | “CONNECT”, “READ”, “CREATE_SUBOBJECTS”, “UPDATE”, “DELETE”, “MODIFY_PERMISSIONS”, “MODIFY_CREDENTIALS” |
| Owner | “CONNECT”, “READ”, “CREATE_SUBOBJECTS”, “UPDATE”, “DELETE”, “MODIFY_PERMISSIONS”, “GRANTAUTH”, “MODIFY_CREDENTIALS” |
| Project Member | “CONNECT”, “READ” |
You can Create a new Role if none of the default roles meet your needs.
First Step is to create the Role
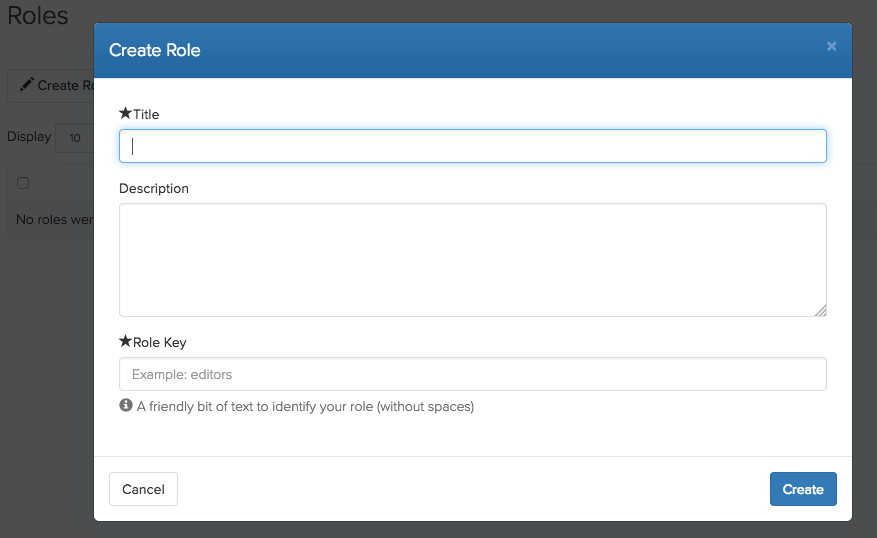
Second Step is to add Permissions to the Roles
- Select Permissions
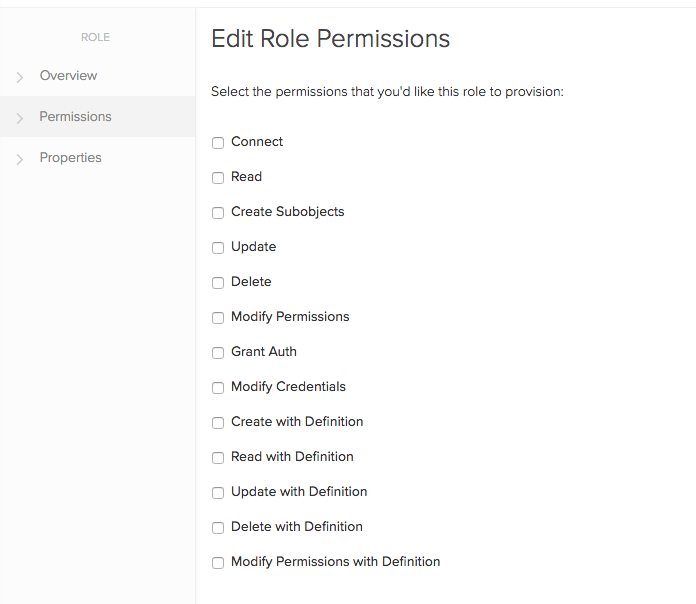
List of Permissions:
| Permission | Description |
|---|---|
| CONNECT | The principal can connect to a Permissioned. This permission supersedes all others. If not granted, the principal is not aware of the Permissioned and can perform no operations against it. |
| READ | The principal can read the Permissioned. |
| CREATE_SUBOBJECTS | The principal can create objects that are contained within the Permissioned. |
| UPDATE | The principal can update the Permissioned. |
| DELETE | The principal can delete the Permissioned |
| MODIFY_PERMISSIONS | The principal can assign, revoke and modify permissions against the Permissioned. |
| GRANTAUTH | The principal can assign impersonating around another principal. This is solely used for Authentication Grants as a means of describing who can create new grants for a principal. |
| MODIFY_CREDENTIALS | The principal can modify the credentials for another principal. This is solely used to describe rights against Identities. |
| IMPERSONATE | The principal can impersonate a target principal. As such, when the principal is signed on, they can take on the authentication credentials of the target principal. |
