Multifactor Authentication
Cloud CMS supports Multifactor Authentication (MFA) to provide enhanced security for your users and their account credentials.
With Multifactor Authentication is enabled for a user, that user will be required to supply a verification code in addition to their username and password. The verification code is delivered to the user's phone or mobile device via SMS, a phone call or an app. The code may also be delivered via a hardware device depending on the kind of provider you configure.
The verification code is required to log in.
This helps to prevent interested parties from stealing your user's Cloud CMS login credentials and prevents them from using those credentials to perform malicious attacks. The regular username and password credentials are still needed, but a verification code is further needed.
And that code is only ever delivered directly to a user's external device (the external "factor").
Providers
Cloud CMS has out-of-the-box support for a couple of common Multifactor Authentication Providers. At least one of these providers must be configured in order for your users to enable MFA login.
If you are an on-premise customer, you may also build your own Multifactor Authentication Providers and configure them into the product using Spring configuration.
Platform Authenticators
You can set up MFA Configuration on the fly for a tenant by setting up a Service Descriptor. Adding a Service Descriptor creates a new Dynamic Authenticator that you can use to authenticate your users to back end authentication providers.
To add an Authenticator, log in to your user interface and go to the Manage Platform section:
And click on Services on the left-hand menu:
This takes you to the Services page:
Click on Add a Service Descriptor. This brings up a modal to help you configure your MFA service.
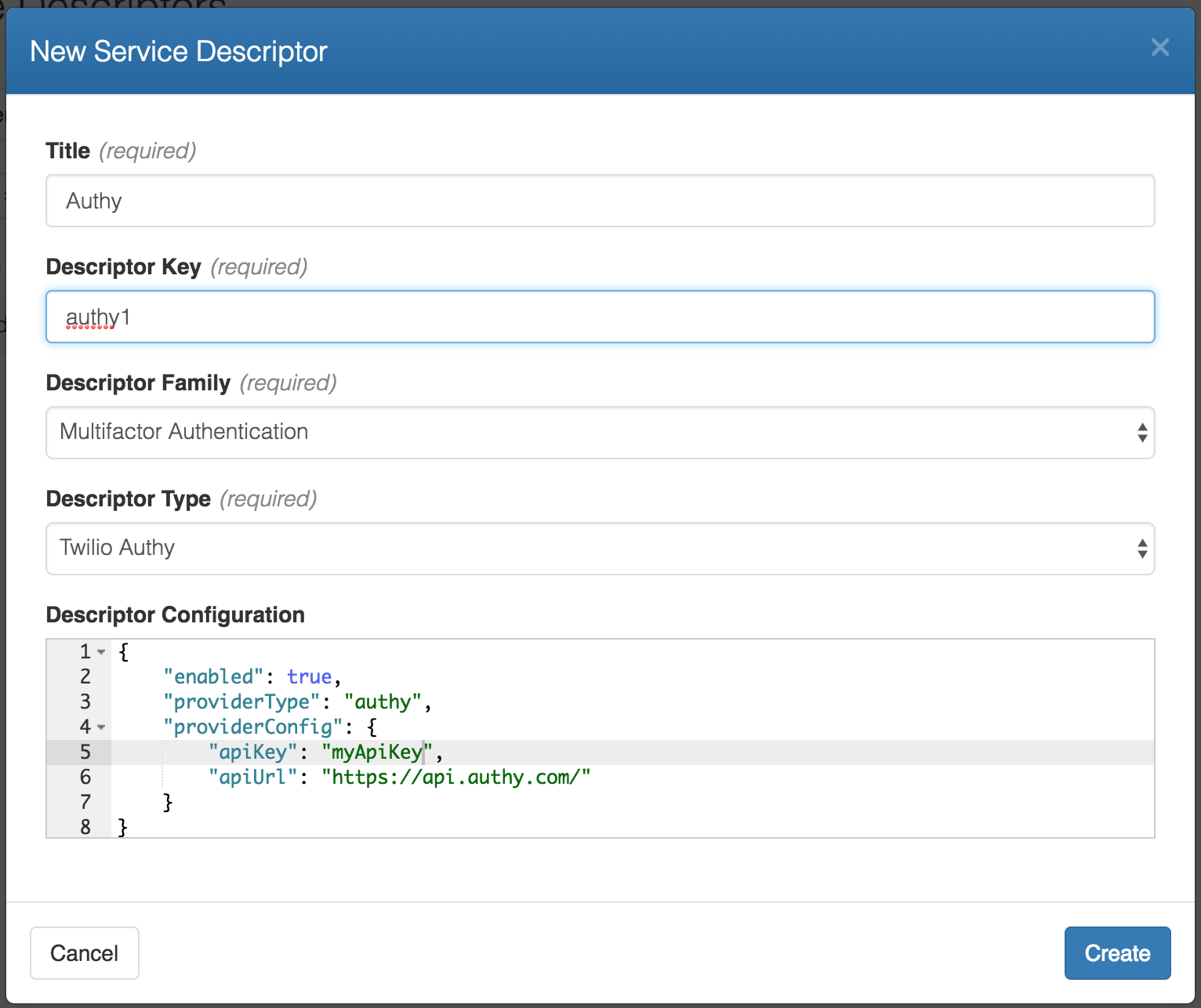
- Give your service a Title and a unique Descriptor Key.
- For Descriptor Family, pick
Multifactor Authentication.
You then need to pick a Descriptor Type and fill in a Descriptor Configuration.
Here is an example configuration for Authy:
Here is an example configuration for Duo Security:
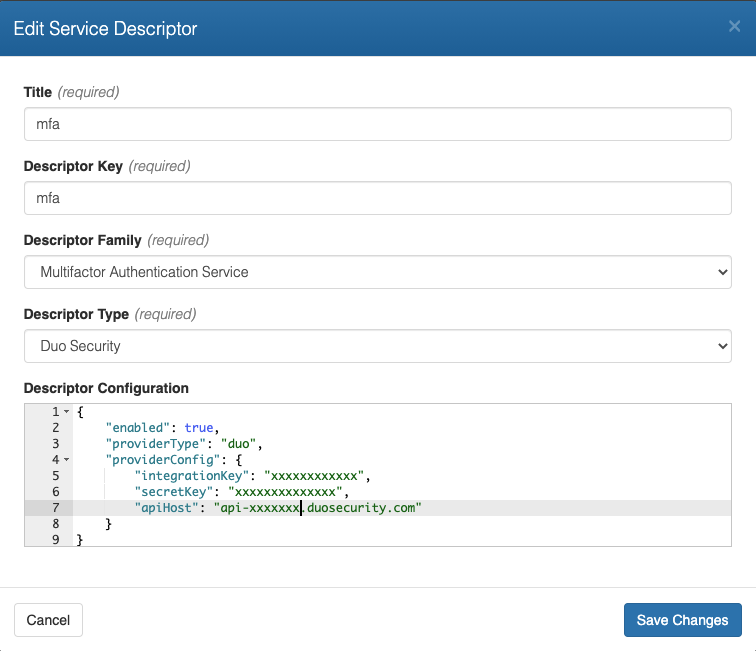
Click Create to create your Authenticator.
The following providers are available. Click into one to learn more about how they should be configured.
Global Configuration
If you are an on-premise customer, you additionally have the option to set up global configurations for MFA that will apply to your users and special situations. You can use this to assign an MFA account for a specific principal, to assign an MFA account for the admin user and to assign an MFA account for any authentication via the backdoor password (if you have this configured).
For information on how to set this up, see our article on API Server Configuration for Docker.
Configuring MFA for a User
To configure MFA for a user, you must first log in as that user and then go to your Account Settings page:
And click on Multifactor Authentication:
If MFA is not currently enabled for your user, you will see a button labeled Enable Multifactor Authentication....
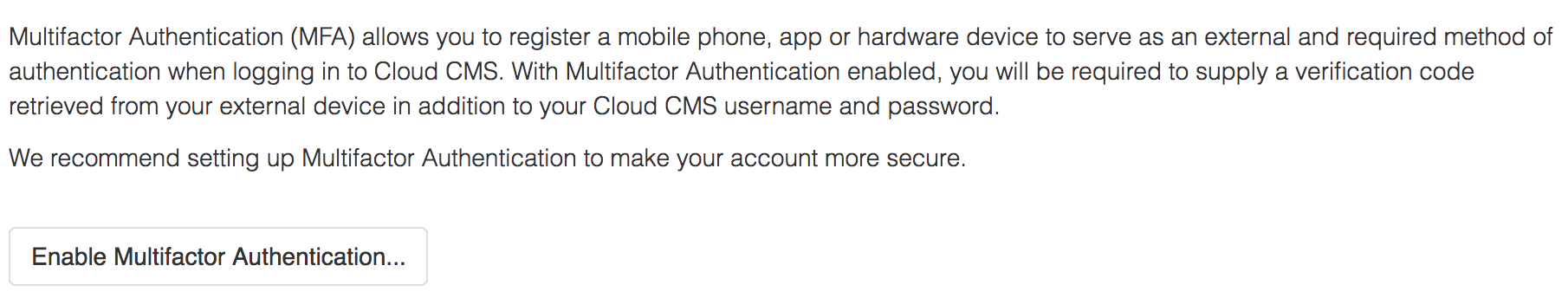
Click on the Enable Multifactor Authentication... button to launch the MFA Setup Wizard.
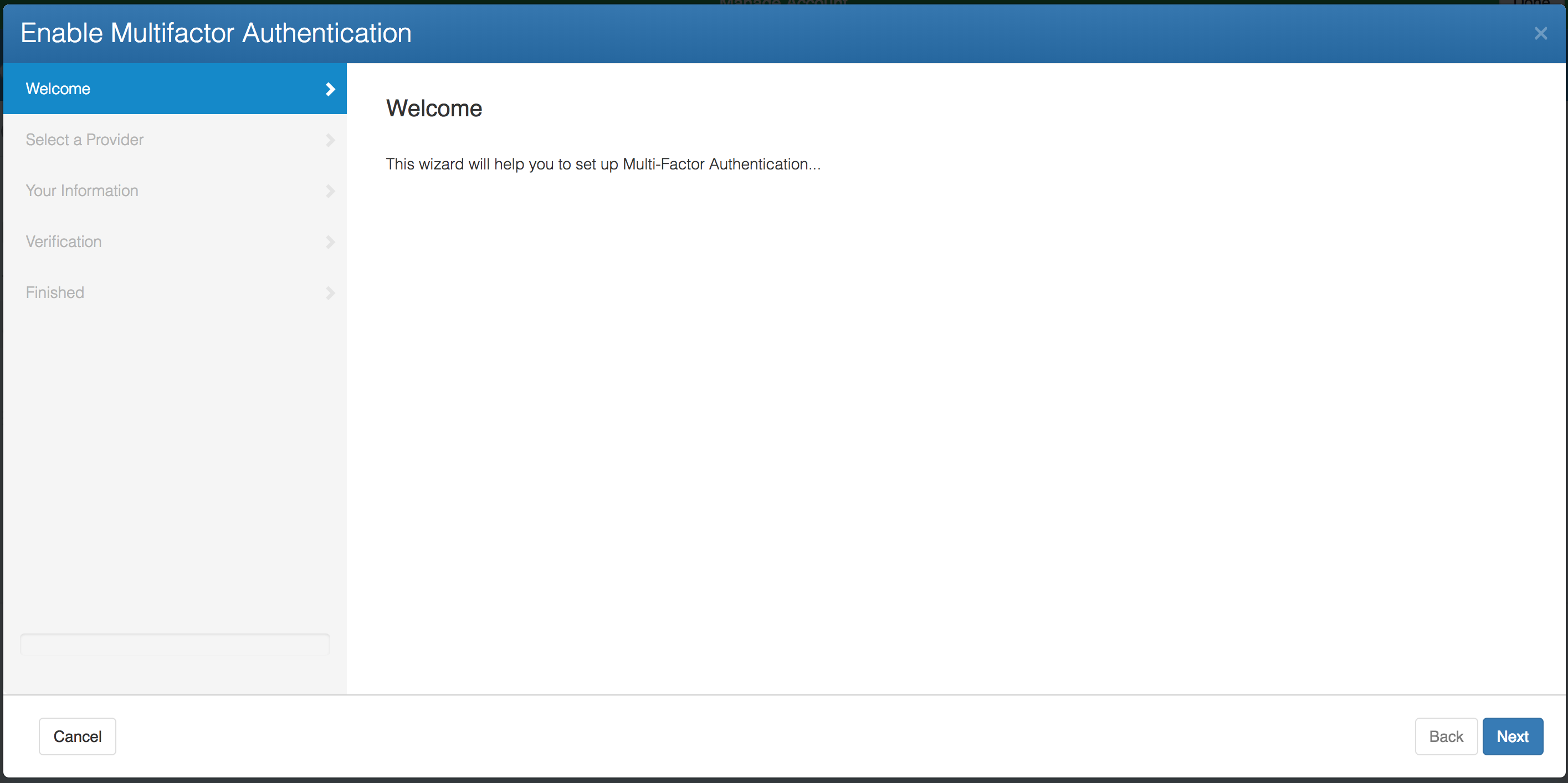
Click Next. You will then be shown a screen where you can pick from the list of configured Authenticators. These are made available by defining a Multifactor Authentication service. See the section on Platform Authenticators above to configure one or more of these.
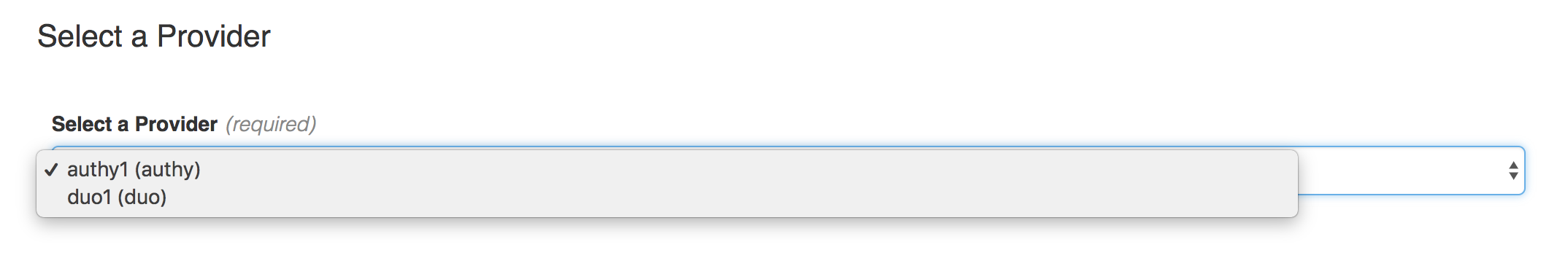
After you've selected your Authenticator, click Next.
Authy
If you select an Authy Authenticator, the next screen will ask you for information that identifies your mobile device.
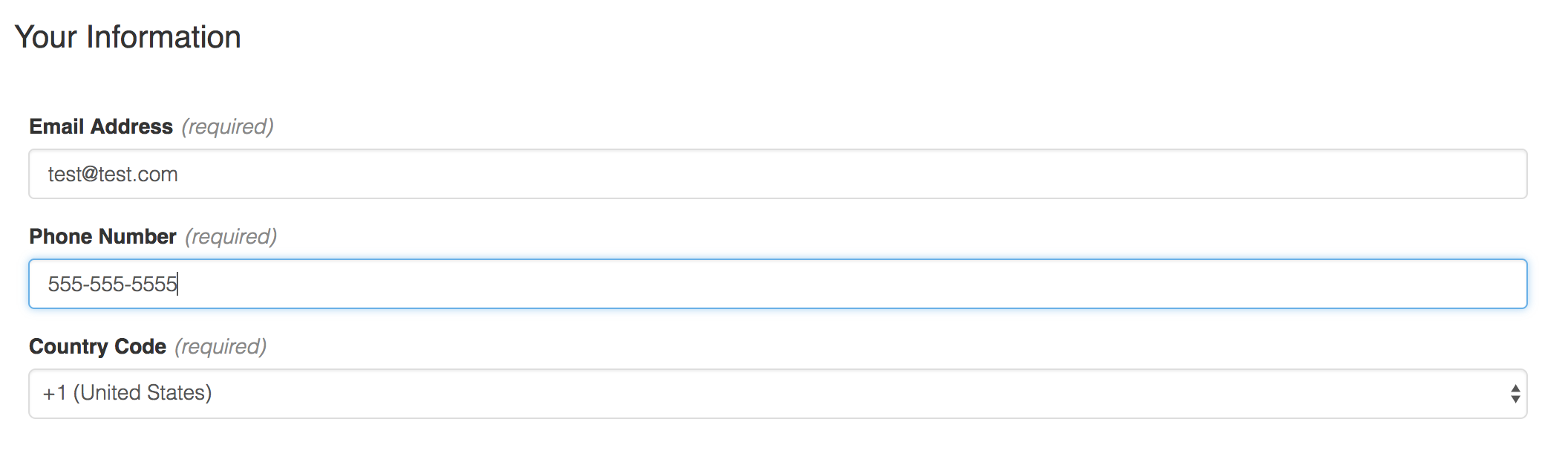
Fill in the required information and click Next.
The wizard will now send a confirmation code to your mobile device. This will be delivered via an SMS text message and will contain a code. When you receive the code, enter it into the wizard.
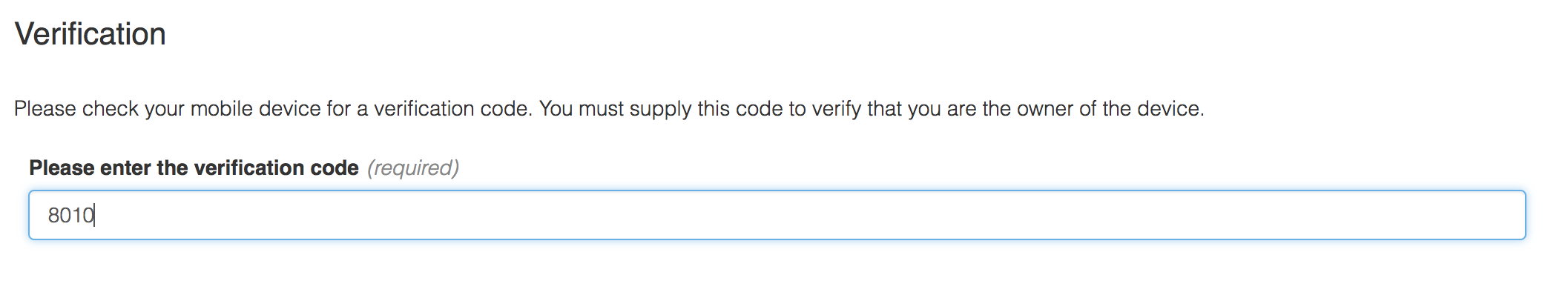
Click Next and the wizard will confirm your code. If your code is successfully confirmed, then your phone will be successfully registered as a second factor for authentication.
Note: Authy provides an optional mobile app that you can use to complete Authy verification -after- the initial registration. This isn't required but if you have it, Cloud CMS will work with it.
Duo
If you select a Duo Security Authenticator, the next screen will present a barcode to you. You will need to scan this barcode into your Duo Security mobile app.
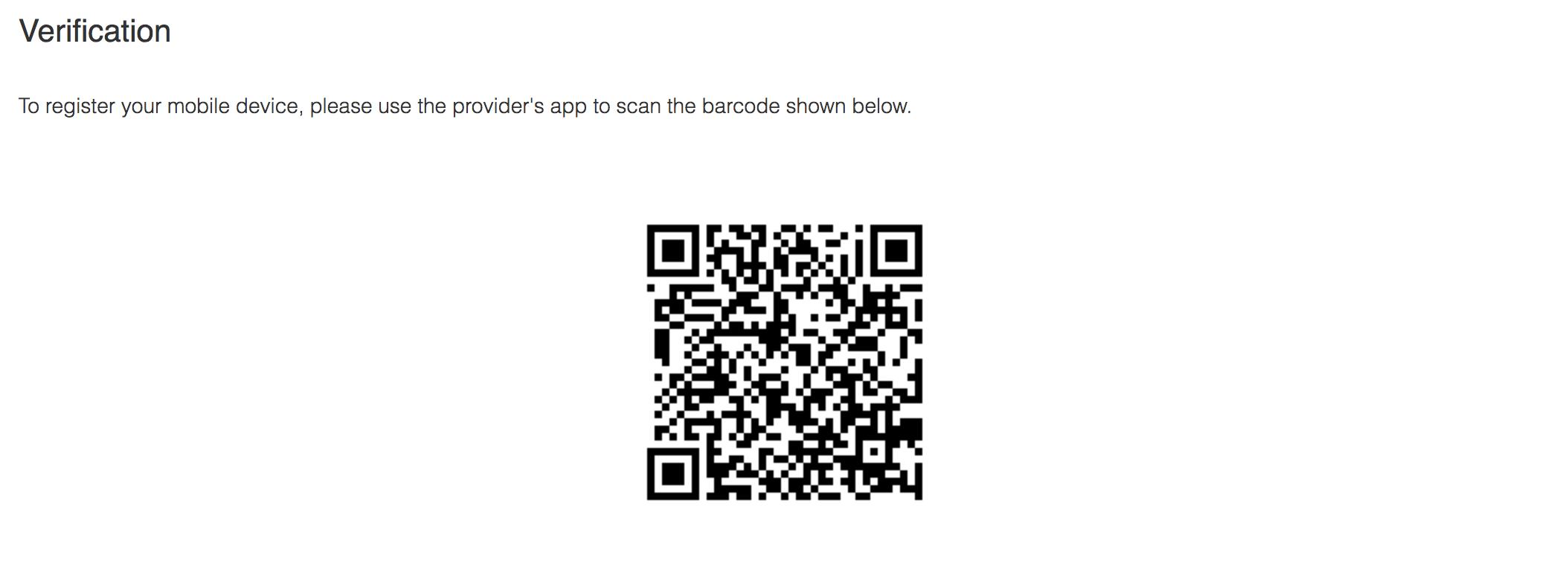
Scanning the barcode will complete the wizard and your phone will be successfully registered as a second factor for authentication.
Note: To use Duo Security, you will need to first install the Duo Security mobile app for your iPhone, Android or other mobile device. Using the mobile app, you scan the barcode and it will complete the registration process seamlessly.
Logging in with MFA
When your account is configured for Multifactor Authentication, you will get a slightly different login experience.
You enter your username and password the usual way:
You will then be prompted to provide your verification code. This will be delivered to your mobile device via SMS or via the mobile app on your phone.
Enter the code and click Verify.
If your code is correct, you will be logged in.


